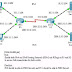
Nowadays when several MAC addresses are associated with one switch port, we cannot assume that this port is connected to another switch or hub as before. It might be connected to a Virtual Machine server.
Do you like this site? Remember to share it to all your friends on Facebook and Twitter!
Monday, October 19, 2009
Friday, October 16, 2009
Wi-Fi Blocking Paint
We know that Wireless LAN (Wi-Fi) is riding on non-licensed bands of radio frequencies. It is unavoidable, especially in a metropolitan area, that our facilities are filled with un-wanted wireless LAN radios.
With new strong encryption, we do not have to worry about the information leakage. However, we DO have to worry about effective transmission throughput. The more users in the same channels, the less effective throughput can we get!
With new strong encryption, we do not have to worry about the information leakage. However, we DO have to worry about effective transmission throughput. The more users in the same channels, the less effective throughput can we get!
Tuesday, October 6, 2009
How to verify the Secondary Root?
As you know we can configure the designated switch as the "Primary root role" or the "Secondary root role" using the following commands:
Although these commands are just "macros" that we cannot see them in the running configuration, it is still easy to verify the "Primary root role" is correctly configured: We just use "show spanning-tree" command to check the designated switch is really the current "Root Bridge".spanning-tree vlan 10 root primay spanning-tree vlan 20 root secondary
Related Posts:
CCNA,
Spanning Tree Protocol
Location:
Wanhua District, Taipei City, Taiwan
Subscribe to:
Posts (Atom)
Popular Posts
-
CCNA Exploration 4.0, Semester 4, "Dual Stack IPv6 and IPv4 configuration " Packet Tracer 5.0 practice file (CNA-04-006). ...
-
I created this practice to test the Packet Tracer 5.3 features of BGP.
-
We hear a lot of directions when we are talking about Data Center technologies: Northbound, Southbound, and even Eastbound/Westbound. What d...
-
Fire-like Kapok blossoms in Taipei City, Taiwan To show the reserved VLAN numbers on both IOS and NX-OS, the common command is: sho...
-
One working switch port on my Cisco Catalyst 2950 suddenly went down by itself! Of course, my phone rang when I was having dinner, and the...