 |
| Screen capture of this alert page. |
If you are running NTP Daemon, remember to upgrade to Version 4.2.7, or just disable “monlist” functionality.
NTP Amplification Attacks Using CVE-2013-5211 | US-CERT:
Overview
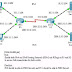
A Network Time Protocol (NTP) Amplification attack is an emerging form of Distributed Denial of Service (DDoS) that relies on the use of publically accessible NTP servers to overwhelm a victim system with UDP traffic.
I believe IT administrators should react immediately even if you run NTP Daemon only inside your corporate network. Any insider knows this caveat could make you in trouble easily.
How to disable "monlist"?
To disable “monlist” functionality on a public-facing NTP server that cannot be updated to 4.2.7, add the “noquery” directive to the “restrict default” line in the system’s ntp.conf, as shown below:
restrict default kod nomodify notrap nopeer noquery restrict -6 default kod nomodify notrap nopeer noquery
Where to get updated NTP Daemon software?
NTP Download Page is here.
References
NTP Amplification Attacks Using CVE-2013-5211 | US-CERT



No comments:
Post a Comment
Tip: you can also anonymously comment here.