[What happened in this incident?]
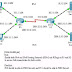
Hackers somehow made some BGP routers of “eNet” to falsely announce that they own the following 5 IP subnets, which are indeed NOT belonging to “eNet”. The true owner is Amazon. To be more specific, they are for Amazon’s Route 53 DNS name resolution services.
- 205.251.192.0/24
- 205.251.193.0/24
- 205.251.195.0/24
- 205.251.197.0/24
- 205.251.199.0/24
The registered domain server for domain “MyEtherWallet.com” is hosted on Amazon Route 53.
Hackers also somehow embedded malicious DNS server (or servers, I really don’t know) also inside service network of “eNet”.
After that, any affected clients’ DNS query for domain “MyEtherWallet.com” would hit hacker’s malicious DNS server. Of course, malicious DNS server would respond with false IP addresses, and those false IP addresses are indeed hacker’s own web servers.
At this moment, clients thought they were accessing “MyEtherWallet.com”, and they indeed were accessing hacker’s web servers.
[Which clients are affected?]
I believe all clients inside “eNet”, and any clients in other Internet Service Providers who trusted “eNet”’s false announcements, would be affected as well.
[Network “eNet” should have been compromised for enough time]
To falsely announce BGP routes, we must either change configurations of hardware routers, or BGP route servers (maybe on Linux).
For me, to configure BGP correctly on a couple of Cisco routers is already a heavy task. It’s not easy. To modify existing BGP configurations to inject false announcements without getting noticed, or without breaking anything at the same time, is even a more difficult task for me.
I really don’t think it would be easier to achieve the same results by working on BGP route servers.
Moreover, hackers even embedded DNS server inside “eNet”’s service network. I really believe hackers had already controlled most of the hardware routers and some hardware servers, maybe for quite a long time, long enough for them to do all such modifications.
I really think some hackers involved in this incident are quite skillful at network hardware maybe Cisco’s or Juniper’s. They could also be CCIEs.
[BGP Injection, instead of BGP Leak]
So, the last thing I want to say is, I would rather call this incident as BGP injection, instead of BGP leak.
Why?
If I hear someone says BGP Leaks, I would feel maybe some unknown bugs inside BGP protocol or some configuration errors caused this incident. As far as I understand now, I really think the false BGP announcements are “intentional”. I would rather say it is BGP Injection.
Although no strong security mechanisms are defined in BGP protocol itself, in this case BGP protocol is not to blame.
 |
| Flowers of East Asian sage, around Zhoumei Xian Zai Gang Park (洲美蜆仔港公園) Taipei City, Taiwan. |
One more thing…
Amazon is also not to blame for this incident. Clients’ DNS query packets never reached Amazon at all.
I suggest Internet Service Providers should pay more attention to the security of their service infrastructure. Don’t become another “eNet”.
I also suggest Internet Service Providers should review their incoming BGP policy. In this case, some ISPs other than “eNet” were also affected because their BGP routers “trusted” “eNet”’s false announcements. They affected their own customers and forwarded that false information on at the same time.




No comments:
Post a Comment
Tip: you can also anonymously comment here.