- CNA-04-005.pkt, (Backup Link)
- CNA-04-005-pat-sample-sol.pkt, (Backup Link)
- CNA-04-005-nat-sample-sol.pkt, (Backup Link)
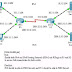
The diagram is the same as the previous post, except that EIGRP between Router R0 and Router R1 is removed, and a new default route pointing to R0 (here it represents the Internet) has been added into R1.
Before we start to configure NAT/PAT, we can easily verify that any PCs or Switches below R1 cannot connect to R0. This is because R0 does not have any route to those network addresses (192.168.X.0/24) below R1. We must successfully configure NAT/PAT to translate all source IP addresses into those in network 10.1.1.0/24 to achieve outbound connectivity to R0 (Internet).
Recall that the 3 basic steps to configure NAT/PAT:
- Specify "Inside" interfaces: source addresses of packets coming through these interfaces need to be translated
- Specify Outside interfaces: destination addresses of packets coming through these interfaces need to be recovered
- Define translation rule: this step is quite different between NAT and PAT. I will discuss PAT and NAT in different sections later
Step 1 and 2 are all the same in all modes:
interface FastEthernet0/0
ip address 192.168.10.1 255.255.255.0
ip nat inside
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 192.168.11.1 255.255.255.0
ip nat inside
duplex auto
speed auto
!
interface Serial0/0/0
ip address 10.1.1.1 255.255.255.0
ip nat outside
clock rate 64000
!
[PAT]
The only difference is at Step 3. Let's start from PAT.
PAT enable us to reuse the IP address of Router R1's "Serial0/0/0" interface for all inside hosts. Since every host is translated into the same IP address, we can only tell which packets should be recovered to which source host by its TCP/UDP port number.
Now, we need ACL here again! We use ACL to classify packets. If the classification result is permit, then it will be translated; otherwise if the result is deny, it will NOT be translated.
Key configuration fragment is as below:
ip nat inside source list 100 interface Serial0/0/0 overload
!
access-list 100 permit ip 192.168.10.0 0.0.0.255 any
access-list 100 permit ip 192.168.11.0 0.0.0.255 any
!
Here is the translation result of PAT. NOTE: If you want to see similar results as I do, you must create some connections outbound to R0, such as TELNET. The screen capture is done when 2 PCs are having 2 active TELNET sessions to Router R0.
R1>show ip nat translation
Pro Inside global Inside local Outside local Outside global
tcp 10.1.1.1:1024 192.168.10.10:1025 10.1.1.2:23 10.1.1.2:23
tcp 10.1.1.1:1025 192.168.11.10:1025 10.1.1.2:23 10.1.1.2:23
R1>
We can see clearly the effect of PAT on Router R0. R0 thought it was 2 connections sourced from 10.1.1.1.
R0>show user
Line User Host(s) Idle Location
* 67 vty 0 idle 00:00:00 10.1.1.1
68 vty 1 idle 00:01:48 10.1.1.1
Interface User Mode Idle Peer Address
R0>
[NAT]
In NAT, each local IP address will occupy one public global address when we configure NAT instead. Here I assume IP addresses from 10.1.1.101 to 10.1.1.200 is reserved as a pool for NAT use.
NOTE: IP address pool here is similar to car parking slot pool. One car, one slot, and in "first-come-first-serve" way. In above example, only the first 100 local hosts making outbound connections will get its own address. If the pool is full, starting from 101st late comer, no new local hosts can be served by NAT and thus cannot make outbound connections at all!
Key configuration fragment is as below:
ip nat pool INET-POOL 10.1.1.101 10.1.1.200 netmask 255.255.255.0
ip nat inside source list 100 pool INET-POOL
!
access-list 100 permit ip 192.168.10.0 0.0.0.255 any
access-list 100 permit ip 192.168.11.0 0.0.0.255 any
!
The screen capture is done as before when 2 PCs are having 2 active TELNET sessions to Router R0.
R1>show ip nat translation
Pro Inside global Inside local Outside local Outside global
--- 10.1.1.101 192.168.10.10 --- ---
--- 10.1.1.102 192.168.11.10 --- ---
R1>
The effect of NAT is clearer on Router R0. R0 thought they were connecting from 10.1.1.101 and 10.1.1.102.
R0>show users
Line User Host(s) Idle Location
* 0 con 0 idle 00:00:00
67 vty 0 idle 00:01:45 10.1.1.101
68 vty 1 idle 00:01:35 10.1.1.102
Interface User Mode Idle Peer Address
R0>




No comments:
Post a Comment
Tip: you can also anonymously comment here.