What I have understood now
The victim is PIR Bank. One of the suspects is MoneyTaker. After the breach, PIR Bank hired company Group-IB to do the clean-ups, recovery, and investigating how the hackers got into their internal network.
Up to this moment, Group-IB disclosed hackers exploited the outdated routers of PIR Bank. The model of the routers was Cisco 800 series routers, which was already declared publicly that the End of Support date would be someday in Year 2016, by Cisco. The running Cisco IOS version was 12.4.
My understanding
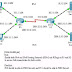
All the routers involved in this incident in my opinion must had been deployed as Internet VPN routers. They must connect directly to the public Internet. Suppose those routers were purely internal routers without public Internet connections at all, hackers can only have access to them by getting through layers of firewalls. Suppose hackers already had broken through layers of firewalls, then hackers could have attacked directly without exploiting any of those outdated routers.
I believe the VPN protocol used should be IPSec. However, IPSec was not to blame for this incident. Vulnerabilities were in the software or the hardware of those installed routers. It might be some discovered vulnerabilities and hackers took advantages of Zero-day Exploits to hack into the network. Hackers either used the hijacked router as a hopping location or changed the access rules so hackers had backdoor accesses to the internal network.
I also want to emphasize that Cisco is not to blame. Cisco had already announced End of Support long time ago. If a customer insisted to keep using the old outdated routers, customers should take most of the responsibilities.
It was a pity for a loss of nearly 1 Million US Dollars. One million dollars is enough to buy and replace a lot of new routers to prevent this loss.
Enterprises should take actions, my suggestions
- Create a complete inventory of routers, especially for those connected to public Internet.
- Confirm with network hardware providers which routers are being or getting out of support. Create schedules to replace them as early as possible.
- Make sure all supported routers are running most up-to-date patched operating systems and software.
 |
| Sun flowers in Taoyuan Agriculture Expo (桃園農業博覽會) 2018. Taoyuan City, Taiwan |
One more thing…
I don't think we should worry about the architecture of Internet VPN and IPSec protocol itself. Many new technologies are relying on Internet VPN and IPSec. For example, Software-defined Wide Area Network (SD WAN) is built on top of Internet VPN and IPSec.
If we make sure all running VPN routers are in healthy condition, Internet VPN architecture is still a cost-effective WAN solution with great flexibilities for enterprises.







No comments:
Post a Comment
Tip: you can also anonymously comment here.