Here are the points I learned from this video. Have fun with it!
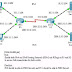
0:13 ASA 1000V is designed for multi-tenant deployment. In this demo, all three customers (tenants) occupy their own ASA 1000Vs.
1:19 ASA 1000V can be deployed as an IPSec VPN tunnel end point. This is a typical scenario for customers to add ASA 1000V. Because they can have their dedicated VPN gateways, they do not have to share VPN gateways at data center side with other customers (tenants).
1:50 ASA 1000V provides IP NAT when customers have to communicate with each other. This is especially true even when all the customers have overlapping IP address spaces.
How would the customers have overlapping IP address spaces? Because we usually automate the deployment of new customers by cloning all virtual machines in a virtualized Data Center as templates on VMware vCenter, all the cloned virtual machines would have exactly the same IP addresses.
3:34 A test client can successfully open web pages on the web server with application service running.
4:17 Another example: clone a existing web server and see the cloned virtual machine will NOT inheritate any permissions from the source web server. Because policy of Virtual Security Gateway (VSG) is “glued” to each single virtual machine, that new cloned server would not get the same permission as its source web server and then be implicitly denied to access that same application server, just like adding normal new server without any security policy configured on it.
Of course, this part of video is demonstrating the functions of VSG, not the ASA 1000V.
6:09 Connecting to the cloned server and we verify the application server connection indeed failed and the error web page shows the connection failure to application server.
6:49 This demonstrates ASA 1000V can protect incoming attacks on the network, and also keep normal clients working at the same time, just like any physical ASA. Two attacks SYN/FIN attack and SYN flooding are performed on the web server and thus hitting ASA 1000V. However, the normal users can still make their good connections to the web server.
8:52 ASA 1000V itself can also be cloned if you have to deploy more customers (tenants), just like other virtual machines.



No comments:
Post a Comment
Tip: you can also anonymously comment here.