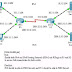
R0>show clock *00:20:29.467 UTC Fri Mar 1 2002 R0>
Reference of show clock on Cisco.com
Symbol
Description
*
Time is not authoritative.
(blank)
Time is authoritative.
.
Time is authoritative, but NTP is not synchronized.
* NOTE: the above table also applies to log messages!